In an era where cyber threats are becoming more sophisticated and frequent, organisations need to prioritise robust security measures. That’s why we have the Visma Cloud Delivery Model (VCDM) in place for all Visma companies seeking reliable, cloud-based solutions.
The VCDM is Visma’s approach to developing, delivering, and operating secure cloud services. It describes how teams should be organised and handle their processes, as well as technical requirements and best practices necessary for successful cloud service delivery. It integrates security measures from both the Visma Security Program (VSP) and The Visma Architecture & Technology Program (VATP) into the core of the delivery model, ensuring that Visma products receive uniform protection against emerging threats. This improves security and safeguards both our valuable assets and customer data.

Where we see the biggest impacts
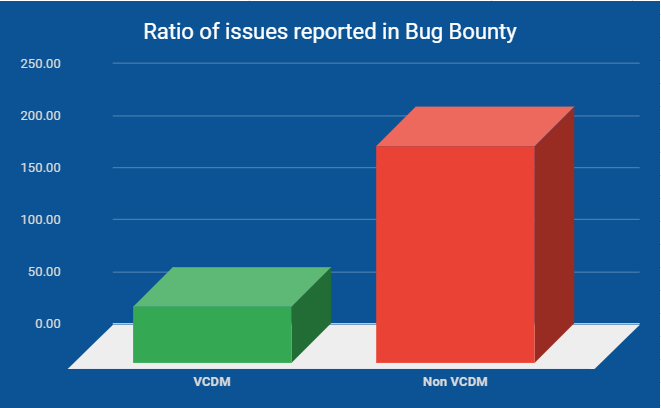
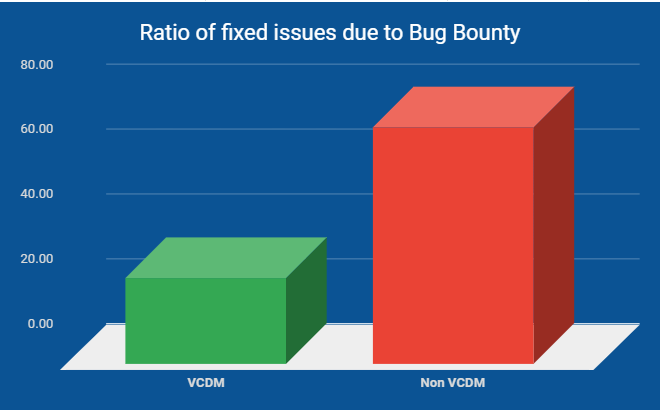
When we look at certain metrics for our products – such as data from our bug bounty program – we clearly see the added value of onboarding to the VCDM.
Our bug bounty program outsources and harnesses the skills of ethical hackers to identify and report potential security vulnerabilities in our products. This program provides comprehensive security testing coverage and is a cost-effective way to find vulnerabilities before they become critical security issues.
Looking at the numbers, we see that Visma products that have been onboarded to the VCDM:
- report fewer vulnerabilities,
- identify vulnerabilities more effectively, and have a faster resolution time,
- encourage a forward-thinking approach to security,
- enable continuous security testing, and
- build trust with their customers.
These products have undergone an extensive onboarding and verification process to become VCDM compliant and are, therefore, considered ideal candidates for such programs.
“The VCDM approved services are very good, and I don’t lose any sleep over their security. I simply know they’re the best, by far.”
Espen A. Johansen, CSO at Visma
Read more about our bug bounty program
Why does it work?
We’ve seen that the number of vulnerabilities on products onboarded to VCDM are significantly less than products not onboarded to it. The big question is: why does a cloud delivery model work so well? Here are a few of the biggest reasons:
- Comprehensive security framework: At Visma, the VCDM is built on a robust and comprehensive security program: the Visma Security Program. It incorporates industry-leading security practices and standards, including continuous monitoring, secure infrastructure, and proactive threat detection mechanisms, among other things. By adopting this program, our products can leverage the inherent security measures we provide, reducing the overall attack surface and minimising the likelihood of vulnerabilities in their products.
- Expert security team: Each of our teams maintain a dedicated security engineer who is well-versed in identifying and mitigating potential security risks. We also have expert security teams that continuously monitor the Visma Cloud environment and possess extensive knowledge of common vulnerabilities and attack vectors. Their expertise in secure coding practices, penetration testing, and vulnerability management enables our developers and security engineers to proactively address potential security issues. By relying on the expertise of our security team, Visma companies can address security vulnerabilities before they’re exposed in a bug bounty program.
- Rigorous testing and validation: The VCDM incorporates rigorous testing and validation processes throughout the software development lifecycle. This includes systematic code reviews, vulnerability scanning, and penetration testing. By putting products through these comprehensive tests, companies can identify and address vulnerabilities before their products are made available for bug bounty programs. This thorough-testing approach significantly reduces the likelihood of discovering severe vulnerabilities during the bug bounty phase.
- Adherence to compliance standards: The VCDM adheres to industry-leading security and compliance standards, such as GDPR, ISO 27001, and ISAE 3402. By onboarding their products to this model, Visma companies inherit the security practices and controls required by these standards. Compliance with such frameworks ensures that security vulnerabilities are minimised and that robust security measures are implemented across the board.
- Continuous improvement: The VCDM, the VSP, and the VATP foster a culture of continuous improvement when it comes to security. We actively incorporate feedback from our bug bounty programs, security researchers, and industry trends to enhance security practices. By being part of such models, our companies benefit from ongoing security updates and refinements based on all of our insights. This iterative approach minimises the likelihood of recurrent vulnerabilities and helps companies stay ahead of emerging threats.
Onboarding products to models like the VCDM gives Visma companies a strong foundation of security measures, access to expert security teams, rigorous testing processes, adherence to compliance standards, and a commitment to continuous improvement. That means these products are designed and developed with security as a core focus from the outset, which is pivotal for navigating the ever-evolving digital threat landscape we’re living in.

